Nearly All Firms Have Ties With Breached Third PartiesNearly All Firms Have Ties With Breached Third Parties
The average organization does business with 11 third parties, and 98% of organizations do business with a third party who has suffered a breach, an analysis finds.
February 1, 2023

Nearly every company does business with — or uses the products of — a third party that has suffered a compromise, thus increasing their security risks.
That's according to data science firm Cyentia Institute, which has issued an analysis that includes external measurements of security from more than 230,000 organizations provided by cybersecurity risk-management firm SecurityScorecard. It found that the average firm had around 10 third-party relationships, and hundreds of indirect fourth-party relationships, with the typical firm having 60 to 90 times more fourth parties than third parties. Nearly all firms (98%) had at least one third-party partner who had suffered a breach, the report stated.
The IT sector has the most third parties, with an average of 25, while the finance sector had the fewest, at 6.5. Those numbers quickly balloon when fourth-party relationships are included, as did their risk. The average firm has an indirect relationship with 200 fourth parties that have had a breach, the analysis found.
The research underscores the sprawling nature of third- and fourth-party relationships for corporations, and the dramatic increase in risk that they can cause, says Wade Baker, founder and partner at the Cyentia Institute.
"Risk goes downhill," he says. "The first parties are more likely to have good security [risk] scores than their third parties, and with fourth parties, the numbers really explode. You need to expect [these firms and products] to not be up to your standards for security."
That's because while many organizations have become more mature regarding their own cyber risks, few are cognizant of the extended risks, Cyentia and SecurityScorecard stated in the analysis.
"Many organizations are still unaware of the dependencies and exposures inherent to third-party relationships, and simply focus on managing their own security posture," the report stated. "Others are aware of those issues, but don't make vendor decisions based on security and/or require vendors to meet certain standards. Even firms that do establish third-party security requirements can struggle to continually monitor compliance and progress."
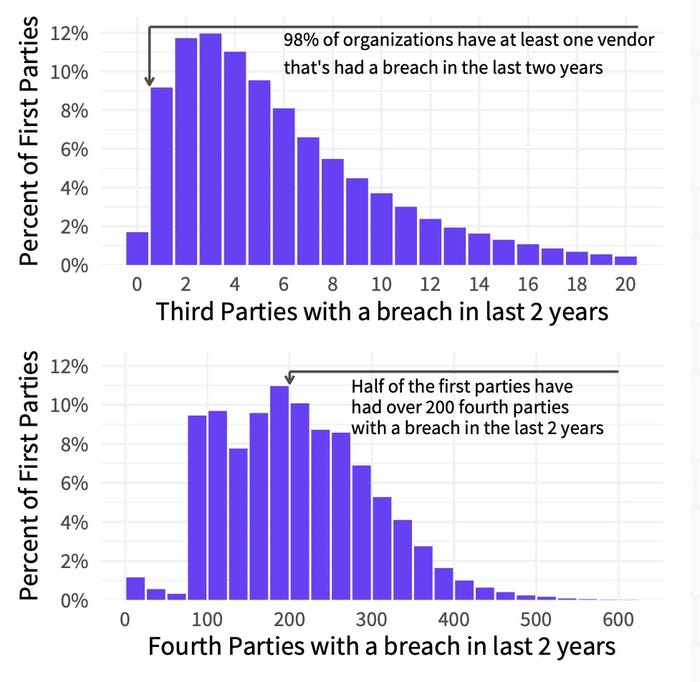
Almost all companies did business with a third party who had been compromised in the past 2 years. Source: Cyentia Institute and SecurityScorecard
Third-party and supply-chain risk have become significant issues in recent years. And CISOs have become increasing wary of their third-party providers, ever since the compromise of an HVAC supplier led to the breach of retail giant Target.
While the analysis looks at third-party risk, the definition of what a third party is extends not just to vendors and partners, but software providers and open source projects. Now-infamous attacks on software suppliers such as SolarWinds, and vulnerabilities in widely used software components such as Log4J, have raised the visibility of the risk that this arena poses.
The top 5 technologies included in third-party relationships within the data are Google Analytics, Google Tag Manager, Amazon Web Hosting, PHP, and Facebook products — all of which were involved in two-thirds (68%) of third-party relationships, the report stated.
"A lot of these third and fourth party relationships [involve us] both agreeing to adhere to certain policies just by virtue of using a product, and now I'm opening up myself to a certain degree of risk," Baker says.
Risk Rises With Each Hop
The analysis also found that third parties typically have a weaker security posture than the companies they served. Overall, there is a much higher likelihood that third parties will have security problems, meaning that companies can't assume that all of their third parties are as diligent about security.
"I view it in the same way as all of us knowing we have too many privileges — in general, people have access to more data than they need to do their job," Baker says. "It would be good to reduce the number of third parties, especially if they're not needed, and also be a little bit more choosy."
The data, however, does not suggest a clear path forward, beside becoming more aware of the problem. Baker does not necessarily recommend, for example, that organizations cut the bottom 25% of their third parties from their business. However, evaluating them more closely or more frequently might be more realistic, he says.
"If we really want to protect our supply chains, we've got to we've got to make the weakest link stronger," Baker says. "And I think the analysis is showing that there's a lot of weak links across third parties and fourth parties, and that is where the challenge lies."
About the Author
You May Also Like
Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025Shift Left: Integrating Security into the Software Development Lifecycle
Mar 5, 2025




_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)