New Report: Inside the High Risk of Third-Party SaaS AppsNew Report: Inside the High Risk of Third-Party SaaS Apps
A new report from Adaptive Shield looks at the how volume of applications being connected to the SaaS stack and the risk they represent to company data.
March 2, 2023

The software-as-a-service (SaaS) app footprint is expanding nonstop at every organization across the globe. Employees are granting third-party apps access to the company's core SaaS apps, like Microsoft 365 (M365) and Google Workspace, causing security risks. Meanwhile, security teams and organizations are unable to track the number of connected apps or quantify the level of risk these apps are causing.
The recently released report from Adaptive Shield, "2023 SaaS-to-SaaS Access Report: Uncovering the Risks & Realities of Third-Party Connected Apps," found an average of 4,371 connected apps in a typical 10,000 SaaS-user organization that are connected to both M365 and Google Workspace. Furthermore, over 89% of third-party apps connected to Google Workspace and 67% of apps connecting to M365 represent a high or medium risk to a company's SaaS data. Disturbingly, many of these apps are granted high-risk permissions that allow them to delete or share confidential and proprietary corporate data.
Providing insights into the unknown SaaS abyss, Adaptive Shield has aggregated anonymized customer data from hundreds of tenants to provide security teams with a realistic view of the ubiquity of third-party apps and explain today's SaaS-to-SaaS realities and risks in depth.
Understanding the Issue
Here's a scenario a typical employee could be facing: Google Docs lacks a native mail merge feature. Users who need this feature can find an app that does this. Mailmeteor, for example, can provide this functionality — and requires the employee to grant permissions enabling it to delete Google spreadsheets and send emails on behalf of the user.
Mail Merge, a different app, requests permission to see, edit, create, and delete all Google Docs documents, all Google Sheets spreadsheets, all Google Slides presentations, and any other Google Drive file. Mail Merge also requests permissions to manage drafts and send email, change settings and filters in Gmail, and run when users are not present.
In this scenario, Mail Merge is a more high-risk app for the employee to install. If a threat actor gained control of their Mail Merge application, they could easily delete, download, or encrypt entire Google Drives containing critical corporate data.
Volume of Third-Party Connected Applications
The sheer volume of third-party apps makes third-party connected apps nearly unmanageable. As companies grow, the number of apps increases in proportion to that growth.
These are the numbers of M365 connected apps on average by company size:
<5,000 users: 522 connected apps
5,000-10,000 users: 1,253 connected
10,000-20,000 users: 3,508 connected apps
Furthermore, apps connected to Google Workspace are significantly higher than M365. As shown in the chart below, these are the numbers of Google Workspace connected apps on average by company size:
<5,000 users: 1,309 connected apps
5,000-10,000 users: 4,216 connected apps
10,000-20,000 users: 13,913 connected apps
Based on these shocking stats, this means that, on average, a company with 1,000 users should expect to see over 600 apps connected to Google and 200 apps connected to M365.
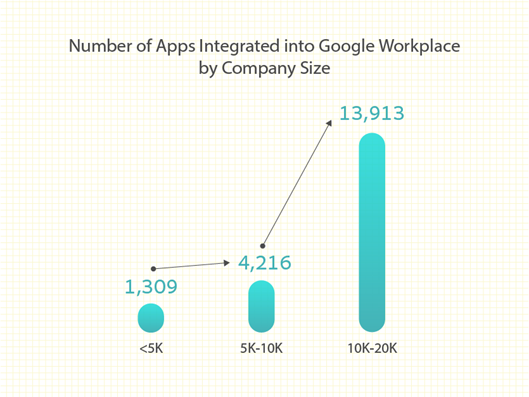
Figure 1: Average number of apps integrated with Google Workspace by users.
A cursory glance at this data might lead one to think that the M365 environment has less cause for concern due to fewer connected applications. However, that is not the case.
While there are more third-party applications typically connected to the Google Workplace, when running the numbers, the amount of oversight and control needed by the security team working with Microsoft and Google to secure the connected apps are on a similar scale.
Risky Permission and Scopes
Every third-party app requests specific permissions when connecting to a SaaS app. The report categorizes these permissions as low, medium, and high risk, based on the types of permissions being requested by the application.
The "2023 SaaS-to-SaaS Access Report" details how 39% of apps connected to M365 are considered high risk, and another 28% are medium risk. Only 11% of apps connected to Google Workspace are high risk, but an overwhelming 78% are medium risk and require access to sensitive permissions.
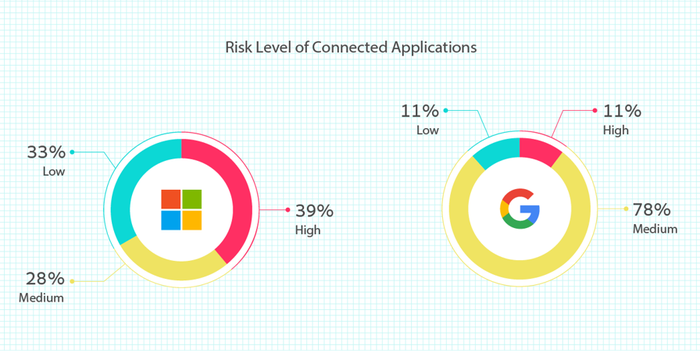
Figure 2. Risk level for apps connected to M365 and Google Workspace
Many applications with high permission scopes are able to read, update, create, and delete content. Apps are often granted full access to mailboxes, and can send emails as the user.
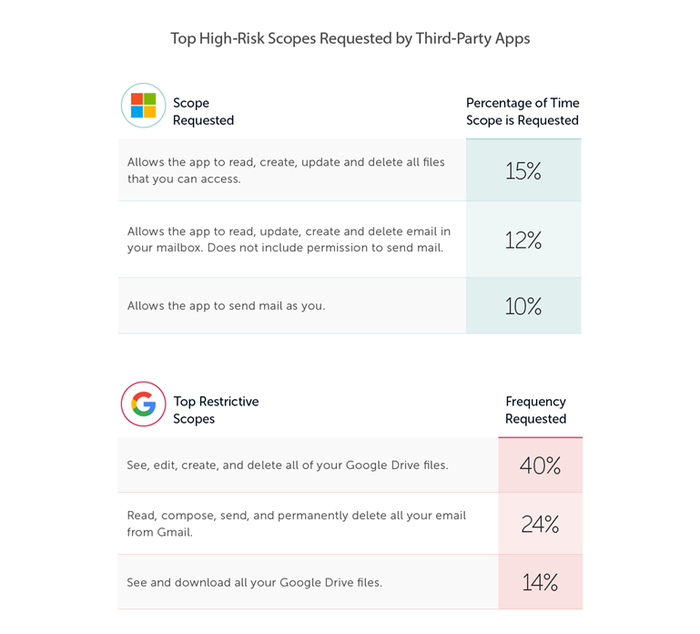
Figure 3: Top 3 high-risk permissions requested by apps connected to M365 and Google Workspace.
These permissions pose a significant risk to the company, as apps can be taken over by threat actors, who can steal, sell, encrypt, or publish the data that they find.
Staying on Top of SaaS-to-SaaS Access
The scope of SaaS-to-SaaS access makes it impossible to manage manually. Organizations trying to control this attack surface and protect data from the risks imposed by third-party apps require an automated tool.
SSPMs automate third-party app monitoring, providing visibility into each app connected to your SaaS stack and the permissions granted to each application.
Download the full report to read all the insights and findings.
About the Author

A former cybersecurity intelligence officer in the IDF, Maor Bin has over 16 years in cybersecurity leadership. In his career, he led SaaS Threat Detection Research at Proofpoint and won the operational excellence award during his IDI service. Maor got his BSc in Computer Science and is CEO and co-founder of Adaptive Shield.
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025

_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)
_Brain_light_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)