Cyber-Insurance Firms Limit Payouts, Risk ObsolescenceCyber-Insurance Firms Limit Payouts, Risk Obsolescence
Businesses need to re-evaluate their cyber-insurance policies as firms like Lloyd's of London continue to add restrictions, including excluding losses related to state-backed cyberattackers.
August 29, 2022

Companies will need to re-evaluate their cyber-insurance premiums after major insurance companies have adopted exclusions for catastrophic cyberattacks conducted by "state-backed" actors.
This limits the risk that companies can offset with cyber insurance, security and risk experts tell Dark Reading — making taking out a policy potentially not worth it.
In the latest limits on cyber policies, insurance marketplace Lloyd's of London issued a notice on Aug. 16 to its member insurers, or syndicates, requiring that they exclude coverage for state-backed cyberattacks. The motive for the additional restrictions is to protect insurance companies and their underwriters from catastrophic loss, and help manage systemic risk that could overwhelm insurers, Lloyd's market bulletin stated.
Is Cyber Insurance Still Worth It?
While the insurers' position is understandable, businesses — which have already seen their premiums skyrocket over the past three years — should question whether insurance still mitigates risk effectively, says Pankaj Goyal, senior vice president of data science and cyber insurance at Safe Security, a cyber-risk analysis firm.
"Insurance works on trust, [so answer the question,] 'will an insurance policy keep me whole when a bad event happens?' " he says. "Today, the answer might be 'I don't know.' When customers lose trust, everyone loses, including the insurance companies."
The cyber-insurance industry has seen profits decline sharply in the past decade, as losses jumped from 35% of the revenue from premiums five years ago, to 72% in 2020. To adapt, insurance companies have dramatically raised the cost of policies — by 74% just in 2021, after rising 22% in 2020, according to FitchRatings.
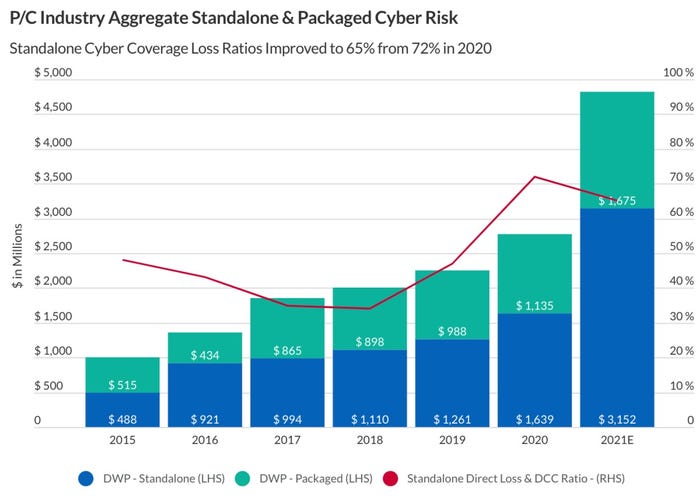
Cyber insurance loss ratios peaked at 72% in 2020. Source: FitchRatings
Yet, insurance firms have also focused on limiting their liability. In 2021, global insurance firm AXA decided to stop paying ransoms to cybercriminals. And over the past two years, insurance companies have added act-of-war exclusions to their policies.
In its market bulletin (PDF), Lloyd's argued that the risk posed by cyberattacks continues to evolve and its members need to adapt to the threats posed by large or widely distributed attacks. While wartime risks are often excluded, Lloyd's requires that syndicates go further and ensure that certain policies have "a suitable clause excluding liability for losses arising from any state-backed cyberattack."
"If not managed properly it has the potential to expose the market to systemic risks that syndicates could struggle to manage," the insurance facilitator stated. "In particular, the ability of hostile actors to easily disseminate an attack, the ability for harmful code to spread, and the critical dependency that societies have on their IT infrastructure, including to operate physical assets, means that losses have the potential to greatly exceed what the insurance market is able to absorb."
The decisions come after pharmaceutical firm Merck won its lawsuit against its insurers after they refused to pay its $1.4 billion in business losses sustained in the NotPetya crypto-ransomware attack in 2017. The judge in the case ruled that the insurance policies' act-of-war exclusion did not apply, because the clause was meant to only exclude losses during armed conflicts.
Regardless, the policy changes are poorly thought out, some argue.
"Signs point to continued breaches and hacks, resulting in a longer claims process, and more litigations," says Goyal. "Unless the industry can collectively fix the way cyber insurance policies are understood, written and priced, ensuring that they are based on actual data and individual organizational risk — one size does not fit all — there is no end to the challenges and mistrust in cyber insurance."
Too Broad an Exclusion
The key problem is that the term "state-backed cyberattack" could be a very broad exclusion, and if abused by the insurance industry, one that will scuttle the usefulness of cyber insurance, experts say.
Attributing an attack to a nation-state is notoriously difficult, says James Turgal, vice president of cyber-risk and strategy for Optiv, a cybersecurity consultancy.
"Even if a computer involved in the attacks was traced back to an IP address located in an Iranian or North Korean military base, that doesn't necessarily mean that it was an attack done with the knowledge of or at the direction of the government's authorities," he says. "It could have been compromised by hackers in other countries [as a false-flag attempt]."
Currently, almost two-thirds of companies — 64% — suspect that they have been either directly targeted or impacted by a nation-state attack, says Kevin Bocek, vice president of security strategy and threat intelligence at Venafi. Many of the major sources of cyberattacks against North American, European, and Asian companies come from cybercriminal groups linked in some way with China, Iran, North Korea, or Russia. Whether that link will equate to being "state-backed" is an open question.
"These companies are clearly going to be worried about whether insurers will deem most attacks to be nation-state sponsored," he says. "As a result, we expect most businesses that are serious about security to double down on their efforts to protect themselves from hackers in the first place."
Insurers will have to develop clear guidelines regarding what evidence and data will be used to determine the attribution of an attack, and what behavior patterns or data points they will consider in determining whether an attack is state-backed, he says.
Time to Beef Up Cyberdefenses
Indeed, the exclusion will likely result in fewer companies relying on cyber insurance as a way to mitigate catastrophic risk. Instead, companies need to make sure that their cybersecurity controls and measures can mitigate the cost of any catastrophic attack, says David Lindner, chief information security officer at Contrast Security, an application security firm.
Creating data redundancies, such as backups, expanding visibility of network events, using a trusted forensics firm, and training all employees in cybersecurity can all help harden a business against cyberattacks and reduce damages.
"Organizations cannot just rely on their cyber insurance policy and must proactively protect themselves from these catastrophic cyberattacks," Lindner says.
Companies also should not expect insurance firms to reverse course. Their approach is just a continuation of the industry's reactive approach to cyber insurance, says Safe Security's Goyal. Insurance firms have increased premiums, put sub-limits on ransomware, and now, have adopted arguably broad exclusions, which may just result in delayed payouts and an increase in lawsuits when insurers refuse to pay out on a large policy.
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025



_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)
_Brain_light_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)