
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
What You Need to Know About PCI DSS 4.0's New RequirementsWhat You Need to Know About PCI DSS 4.0's New Requirements
The updated security payment standard's goal is to “address emerging threats and technologies and enable innovative methods to combat new threats” to customer payment information, the PCI Security Standards Council says.
The PCI Standards Security Council (PCI SSC) published the latest update to the PCI Data Security Standard (PCI DSS) this week. The gold standard for retailers and financial organizations when it comes to protecting sensitive cardholder data, PCI DSS v4.0 shifts the standard's focus to outcome-based requirements.
Much has changed since the preceding version of the standard, v3.2.1,was published back in 2018. Fueled by the pandemic, online transactions and the use of point-of-sale (PoS) machines have skyrocketed, technology has evolved, and cloud platforms are used extensively for storing cardholder data. Attackers have also advanced their tactics targeting the payments industry.
What Is New in PCI DSS 4.0?
The 12 core PCI DSS requirements did not fundamentally change with PCI DSS v4.0, and they remain the critical foundation for securing payment card data. However, the requirements have been redesigned to focus on security objectives to guide how security controls should be implemented.
The key high-level goals for PCI DSS v4.0 are:
Ensure the standard continues to meet the security needs of the payments industry.
Add flexibility and support of additional methodologies to achieve security.
Enhance validation methods and procedures.
Even though PCI DSS 4.0 keeps the existing prescriptive method for compliance, the new version introduces an alternate option for meeting compliance: customized implementation. Customized implementation considers the intent of the objective and allows entities to design their own security controls to meet it. This change will allow businesses to modify implementation procedures and meet requirement intent.
Stronger Authentication Requirements
Identity and access management (IAM) plays a crucial role in safeguarding cardholder data, and the new version of the standard recognizes that.
PCI DSS 4.0 aligns with the NIST guidance on digital identities for authentication and life cycle management. As the payments industry has gradually moved to the cloud, stronger authentication standards to payment and control access logins are necessary. PCI DSS 4.0 considers:
Multifactor authentication (MFA) usage for all accounts that have access to the cardholder data, not just administrators accessing the cardholder data environment.
Passwords for accounts used by applications and systems must be changed at least every 12 months and upon suspicion of compromise.
Use of strong passwords for accounts used by applications and systems, which must contain at least 15 characters, including numeric and alphabetic characters. PCI DSS requires that the prospective passwords be compared against the list of known bad passwords.
Access privileges must be reviewed at least once every six months.
Vendor or third-party accounts may be enabled only as needed and monitored when in use.
The PCI DSS 4.0 standard is built with a zero-trust mindset, permitting organizations to build their own unique, pluggable authentication solutions to meet the data security regulatory requirements. At the same time, authentication methods can scale to fit the company’s transaction objectives and risk environment. Finally, PCI SSC has partnered with Europay, Mastercard, and Visa to implement the use of the 3DS Core Security Standard during transaction authorization.
Expanded Applicability of Data Encryption
The latest standard considers broader applicability for encrypting cardholder data, now expanding on trusted networks. In addition, the requirement for data discovery to locate all sources and locations of cleartext primary account numbers (PAN) will be more frequent, at least once every 12 months and upon significant changes to the cardholder data environment or processes. The rationale is that malicious code is one of the biggest problems that financial institutions face. Once the code embeds in the network, information can be retrieved through cardholder data transmission.
Introducing the customized implementation approach to PCI DSS 4.0 gives businesses more flexibility. Organizations are no longer forced to follow the methods prescribed by the standard or implement a burdensome compensating control, and they can focus on selecting and implementing solutions that achieve the intended outcome of a specific PCI DSS objective. Effective IAM and MFA combined with encryption is the overarching principle behind zero-trust security for protecting sensitive cardholder data and online payments.
Timeline to PCI DSS 4.0
The standard's v4.0 updates don’t immediately come into effect for all organizations. To support the adoption of PCI DSS around the globe, the standard and summary of changes will be translated into several languages, and these translations are set for publication over the next few months, between now and June 2022.
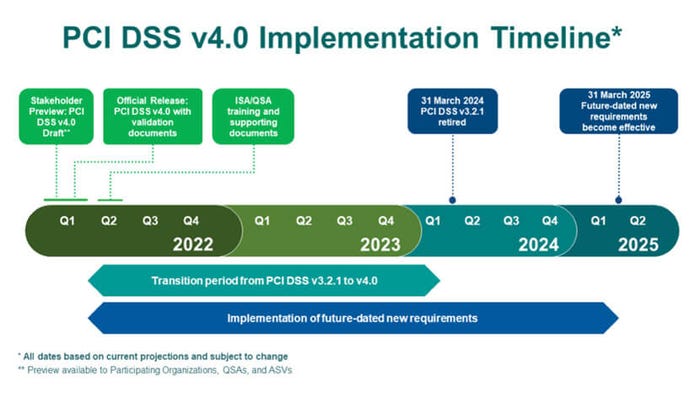
Source: PCI SSC
When it comes to transitioning to the new version, “PCI DSS v3.2.1 will remain active for two years after v4.0 is published,” says PCI SSC. This transition period, ending March 31, 2024, gives organizations time to familiarize themselves with the changes, update their reporting templates and forms, and plan for and implement changes to meet updated requirements. At that time, PCI DSS v3.2.1 will be retired, and v4.0 will become the only active version of the standard.
About the Author
You May Also Like
Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025Shift Left: Integrating Security into the Software Development Lifecycle
Mar 5, 2025

