
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
Cybercriminals Weaponizing Ransomware Data for BEC AttacksCybercriminals Weaponizing Ransomware Data for BEC Attacks
Attacked once, victimized multiple times: Data marketplaces are making it easier for threat actors to find and use data exfiltrated during ransomware attacks in follow-up attacks.

Cybercriminals and other threat actors are increasingly using data dumped from ransomware attacks in secondary business email compromise (BEC) attacks, according to new analysis by Accenture Cyber Threat Intelligence.
The ACTI team analyzed data from the 20 most active ransomware leak sites, measured by number of featured victims, between July 2021 and July 2022. Of the 4,026 victims (corporate, non-governmental organizations, and governmental entities) uncovered on various ransomware groups’ dedicated leak sites, an estimated 91% incurred subsequent data disclosures, ACTI found.
Dedicated leak sites most commonly provide financial data, followed by employee and client personally identifiable information and communication documentation. The rise of double extortion attempts – where attack groups use ransomware to exfiltrate data and then publicize the data on dedicated leak sites – has made large amounts of sensitive corporate data available to any threat actor. The most valuable types of data most useful for conducting BEC attacks are financial, employee, and communication data, as well as operational documents. There is a significant overlap between the types of data most useful for conducting BEC attacks and the types of data most commonly posted on these ransomware leak sites, ACTI said.
The data is a “rich source for information for criminals who can easily weaponize it for secondary BEC attacks,” ACTI said. “The primary factor driving an increased threat of BEC and VEC attacks stemming from double-extortion leaks is the availability of [corporate and communication data].”
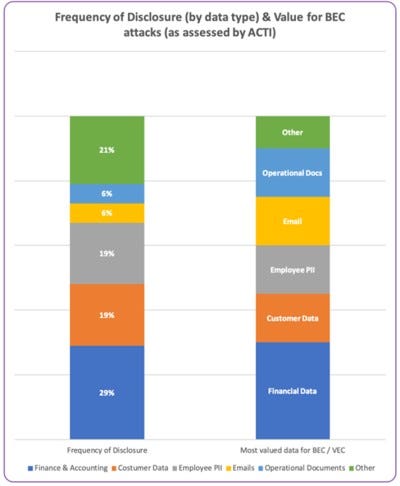
There is overlap between available disclosed data and such data’s usefulness for BEC attacks.
Data thieves are making it easier for their customers to find and access the stolen information. The dedicated leak sites are increasingly available on publicly accessible sites, not hidden away on Tor domains, and some offer searchable indexed data to make it easier for threat actors to find what they need for their attacks.
For example, the operators of the data-selling marketplace Industrial Spy organize and name folders with labels that reflect their content to make finding specific files easy, ACTI said. Customers can use the marketplace’s search functionality to find specific files, such as employee data, invoices, scans, contracts, legal documents, and email messages. The search can also hunt for data from specific industries and countries.
“Indexed and searchable databases like these help actors more efficiently acquire specific data versus downloading bulk data and hoping to find desired information,” ACTI said.
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025

