ESET-Branded Wiper Attack Targets Israel; Firm Denies CompromiseESET-Branded Wiper Attack Targets Israel; Firm Denies Compromise
The security firm is denying an assessment that its systems were compromised in Israel by pro-Palestinian cyberattackers, but acknowledged an attack on one of its partners.
October 18, 2024

Security firm ESET is refuting reports that cyberattackers compromised its platforms and used them to target customers in Israel with dangerous wiper malware. However, it did note that a partner there, Comsecure, was impacted.
"We are aware of a security incident which affected our partner company in Israel last week," the firm acknowledged on social media platform X. "Based on our initial investigation, a limited malicious email campaign was blocked within ten minutes. ESET technology is blocking the threat and our customers are secure. ESET was not compromised and is working closely with its partner to further investigate and we continue to monitor the situation."
Security researcher Kevin Beaumont (aka Gossi the Dog) prompted the response after blogging about a malicious email that an ESET user posted on the ESET user forum. The email was flagged as malicious, with the subject line, "Government-Backed Attackers May Be Trying to Compromise Your Device!" It purported to be from the ESET team, offering extra security defense in the face of an ongoing attack:
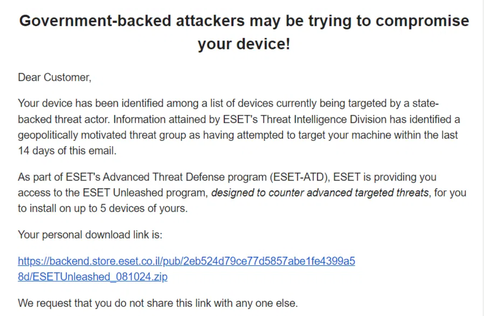
Source: ESET user forum.
The email had a .ZIP attachment that, if opened, unpacked a destructive wiper malware that bears resemblance to that used by the Handala threat group, according to the person who flagged the email for Beaumont. Handala, so named for the political cartoon character that has come to personify the Palestinian people’s national identity, is known for targeting Israeli organizations with file-destroying wipers in the wake of the Oct. 7 Hamas attacks and resulting war.
Beaumont noted, "I managed to obtain the email, which passes both DKIM and SPF checks for coming from ESET’s store," he said in the blog post. "Additionally, the link is indeed to backend.store.eset.co.il — owned by ESET Israel."
This led Beaumont to conclude via Mastodon, "ESET Israel definitely got compromised, this thing is fake ransomware that talks to an Israeli news org server for whatever reason."
ESET has now categorically refuted that takeaway, so the assumption is that the cyberattackers were using some sort of MO to get around anti-spoofing measures for the email and the .ZIP link. ESET did not immediately return a request for comment from Dark Reading for more information on Comsecure's role in the incident and the attack routine.
The campaign is now blocked for ESET customers.
Read more about:
DR Global Middle East & AfricaAbout the Author
You May Also Like
Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025Shift Left: Integrating Security into the Software Development Lifecycle
Mar 5, 2025




_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)