
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
Analysis Shows Attackers Favor PowerShell, File ObfuscationAnalysis Shows Attackers Favor PowerShell, File Obfuscation
Aiming to give threat hunters a list of popular attack tactics, a cybersecurity team analyzed collections of real-world threat data to find attackers' most popular techniques.
December 14, 2022

An analysis of threats encountered by four organizations has identified the most common techniques used by attackers to compromise systems, infiltrate networks, and steal data, according to data analysts at Splunk SURGe, which published details of the research on Dec. 14.
The analysis used published data from Mandiant, Red Canary, MITRE's Center for Threat Informed Defense, and the US Cybersecurity and Infrastructure Security Agency (CISA) to find the most popular post-compromise threat activities, as defined by the MITRE ATT&CK framework. Threat groups that gain access to a compromised system, for example, are likely (28% of the time) to start up the PowerShell command line utility to extend their attack laterally throughout a network and to gain persistence on the compromised machine, the analysis found.
The use of PowerShell, obfuscating files, and exploiting public-facing applications are the three most popular techniques for attackers, the analysis found. Using the data, security operations center (SOC) managers can ensure that they are focused on detecting common tactics, says Ryan Kovar, distinguished security strategist and leader of Splunk’s SURGe research team.
"A lot of times, SOC analysts don't know where to start, and these are the areas where four trusted sources are saying they see adversaries consistently using these techniques," he says. "I talk to a lot of people around the world, and they do not have logging turned on for PowerShell, and if you do not have logging for PowerShell you are never going to see what is arguably the No. 1 adversary technique according to these four groups."
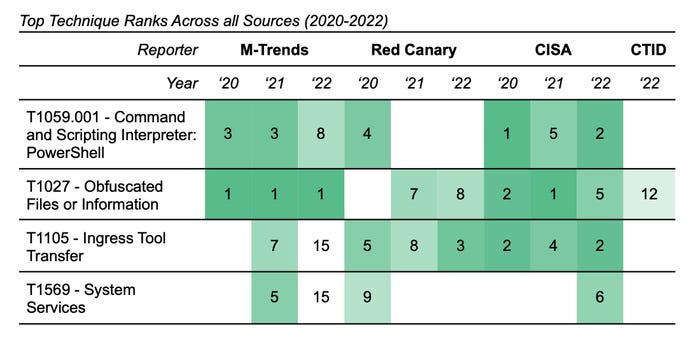
The rankings of the top four techniques by data set. Source: Splunk
The analysis effort combined data on cyberattacks from multiple industries and multiple years, including more than 400 techniques from the MITRE ATT&CK framework and more than 100 techniques targeting industrial control systems (ICS).
The analysis comes at a time when attackers are shifting toward using more stealthy tactics and hands-on intrusion techniques, making the training of SOC analysts increasingly important. In the past year, for example, cybersecurity services firm CrowdStrike has seen a small but measurable increase in targeted attacks, which now account for 18% of all attacks. In addition, attackers are eschewing malware in their attacks, with 71% of intrusions investigated by the firm not using malicious tools.
For defenders, finding ways to detect attacks remains difficult, Splunk researchers stated in the analysis.
"It has never been more difficult to decide which threats deserve the most attention," the analysis stated. "A sound defensive approach to directing analysis efforts should be data-driven, focusing on the trends and progression of attacker tradecraft, such as represented in ATT&CK."
PowerShell, Obfuscated Files Top Tactics
The top four tactics used by intruders includes using PowerShell as a command shell and script interpreter and attempting to obfuscate files and commands to remain stealthy. Using vulnerabilities in public-facing applications is the third most common technique, while spear-phishing attacks are the No. 1 initial access technique, according to Splunk's analysis.
The company plans to expand the list to a top 20 most common tactics, allowing security teams to discuss whether they can detect the techniques and how best to use their current tools to do so.
A critical part of the effort should be to game out each technique, how it could be detected, and whether the current information, telemetry, and logs are able to detect attackers who use the technique. Determining which logs and telemetry to track is the hard part, Kovar says.
"Find all the ways to log and show that information because every vendor and company has such different information and different platforms," he says. "That is where the hard work comes in, and for a lot of people, they know what they want to do, but they just don't know where to start."
Easing the Pain for Threat Hunters
By focusing on the attack techniques most commonly used by attackers, SOCs and security teams should have more information about how to improve their programs and better detect attackers.
Easing the work of SOC analysis is critical. A year-old survey found that 72% of SOC analysts rated the pain of doing their jobs at least a 7 out of 10.
In the end, Splunk's SURGe team aims to give cybersecurity professionals a way to harden their networks against attacks. Tackling the top 20 list of attacker tactics and ensuring that the SOC can detect every technique is a great way to begin 2023, Kovar says.
"Your mileage may vary," he adds, "but I am very confident that if you want to start your threat hunting program in a couple areas and want an immediate return on investment, this is where you can start."
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025

