
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
Monitoring Changes in KEV List Can Guide Security TeamsMonitoring Changes in KEV List Can Guide Security Teams
The number of additions to the Known Exploited Vulnerabilities catalog is growing quickly, but even silent changes to already-documented flaws can help security teams prioritize.
August 7, 2024

B-SIDES LAS VEGAS – Las Vegas – Wednesday, Aug. 7 – Organizations that use the Known Exploited Vulnerabilities (KEV) catalog to prioritize patching are likely missing silent changes to the list that could indicate that an issue's severity has changed, according to an analysis presented at the BSides Las Vegas conference on Aug. 7.
The KEV catalog — which currently consists of more than 1,140 vulnerabilities that are known to have been exploited in the wild — tracks software flaws by their Common Vulnerabilities and Exposures (CVE) identifier, records the date when the vulnerability was confirmed in the wild and has a flag that indicates whether ransomware groups are using the security issues.
Yet, specific changes to the data — such as uncommonly short times to remediate vulnerabilities and changes to the ransomware status — can give security teams valuable information, the analysis stated.
Unfortunately, the Cybersecurity and Infrastructure Security Agency (CISA), which manages the list, does not often call out these changes and outliers, says Glenn Thorpe, senior director of security research and detection engineering at GreyNoise Intelligence.
"We who are not bound by its directives forget that this is actually a to-do list," he says, adding: "So, if folks are actually using this to prioritize remediation or some kind of process, they need to know [when] it is updated silently."
The KEV catalog, introduced in November 2021 with 290 exploited vulnerabilities, is maintained by CISA and gives organizations the information necessary to prioritize patching flaws that are currently under attack. The list, however, does not rank the severity of issues, and vulnerabilities are often not added until well after the initial evidence of exploitation comes to light.
Surge From a Cyber Conflict
While less than 3 years old, the KEV catalog has already passed through three periods, Thorpe says. The original catalog had 287 vulnerabilities, which had an average age — the time between the release of the CVE and the vulnerability's addition to the KEV list — of 591 days. Then, during a 109-day period in early 2022 and the initial months of Russia's invasion of Ukraine, a massive stockpile of vulnerabilities was exploited, encompassing 396 issues with an average age of 1,898 days.
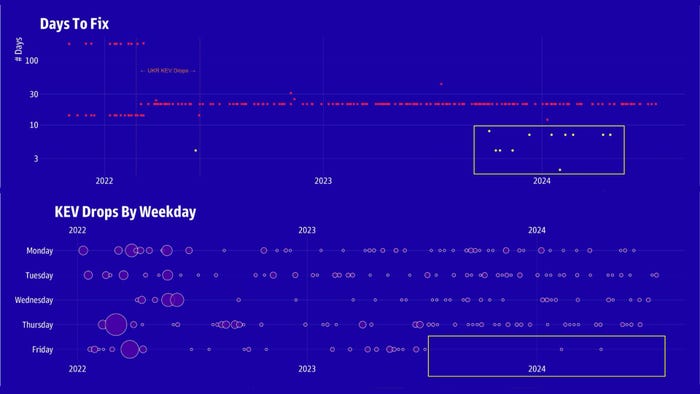
Starting in mid- to late 2023, CISA started changing its policies on the KEV catalog, providing additional signals as to the severity of a vulnerability. Source: GreyNoise Intelligence
Since mid-2022, 453 newly exploited vulnerabilities have been discovered, with an average age of 567 days.
"There is this thought that maybe the numbers have gone down, because the Russia-Ukraine conflict has dragged on so long," he says. "But I [feel that] when it ends, each side will looking for vulnerabilities and stockpiling once again."
Five organizations — Microsoft, Apple, Cisco, Adobe, and Google — account for about half of all vulnerabilities on the list, demonstrating cyberattackers' penchant for major software platforms.
Pay Attention to Friday Updates
While any vulnerability in the KEV catalog should likely be patched as soon as possible, companies may want to prioritize those being used in ransomware campaigns. The list has a flag designating whether CISA has confirmed use of a particular flaw by ransomware gangs. However, at least 41 times, that flag has been changed to "known" — indicating ransomware use — after the vulnerability's addition to the list without explicit notification.
Perhaps more critical for prioritization is the "due date" for fixing a vulnerability, which informs federal agencies of the date by which the issue must be remediated. While the vast majority of vulnerabilities have a 21-day requirement, since late 2023, CISA has set shorter remediation deadlines for specific vulnerabilities. The shorter patching deadlines are typically for more critical appliances that are connected to a networks, such as the severe Ivanti vulnerabilities, as well as issues in Juniper routers and Cisco devices and Atlassian's Confluence server, GreyNoise's Thorpe says.
In fact, another data point suggests that CISA made other changes to how it handles KEV-catalog announcements in late 2023. Around the same time that CISA had assigned shorter deadlines, the agency also began foregoing the release of any list updates on Fridays, except in two specific cases, the analysis found.
"Either there was a decision made to prioritize these a little differently, or they ... were kind of figuring out how to prioritize these differently, because the list is getting big," Thorpe says.
Organizations can use the policy changes inferred from the way CISA updates the KEV catalog to understand which issues the agency considers most critical. A KEV update released on a Friday should be considered significant, as should a vulnerability with a due date less than 21 days away. Finally, Thorpe says, updates to the known ransomware usage field are another signal that security teams should pay attention to.
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025

