Critical Automated Tank Gauge Bugs Threaten Gas InfrastructureCritical Automated Tank Gauge Bugs Threaten Gas Infrastructure
The security vulnerabilities could lead to everything from gas spills to operations data disclosure, affecting gas stations, airports, military bases, and other hypersensitive locations.
September 24, 2024

Multiple critical security vulnerabilities in automatic tank gauge (ATG) systems, some unpatched, threaten critical infrastructure facilities with disruption and physical damage, researchers are warning.
ATGs are sensor systems that monitor and manage fuel storage tanks to ensure that fill levels aren't too low or too high, to see that leaks are detected in real-time, and to manage inventory. ATGs can be found where you'd expect them to be, like at gas stations and airports, but also in less obvious installations.
"In the US, for example, we were told that you are required by law to have an ATG system installed in any fuel tank of a certain size," Pedro Umbelino, principal research scientist at Bitsight's TRACE unit, explains to Dark Reading. "Gas stations are the largest and most obvious use case, but the second largest use case for ATGs are critical facilities that require large backup generators — you often see these in facilities like hospitals, military installations and airports."
Worryingly, most of the newly discovered vulnerabilities allow for an attacker to have full control of an ATG as an administrator. And according to Umbelino, the 11 bugs across six ATG systems from five different vendors can thus open the door to a gamut of nefarious activities, ranging from making fueling unavailable to wreaking environmental havoc.
"What's even more concerning is that, besides multiple warnings in the past, thousands of ATGs are still currently online and directly accessible over the Internet, making them prime targets for cyberattacks, especially in sabotage or cyberwarfare scenarios," Umbelino said in an analysis released on Sept. 24.
The bugs were discovered six months ago, with Bitsight, the US Cybersecurity and Infrastructure Security Agency (CISA), and the affected vendors working in tandem to mitigate the problems. As a result of those efforts, "Maglink and Franklin have released patches," Umbelino says. "The affected OPW product has been EOL'd [end of life] and is no longer being supported by the vendor, so they will not be releasing a patch. Proteus and Alisonic have not engaged with us or with CISA as part of the disclosure process, so it's unclear to us if they’ve released or are working on a mitigation plan."
Patching isn't where the remediation needs stop, though.
"Even for devices that have had patches issued, my top recommendation is to disconnect these devices from the public Internet," Umbelino says. "Most of them were never designed to be connected in the way they are today, so they weren't built with the level of security that is required for Internet-connected devices. They're being used in ways that vendors hadn't initially intended, and that's what is at the core of these vulnerabilities. Taking them off the public Internet is the only true solution."
Major Cyber-Risk From ATG Tampering
ATGs not only automatically measure and record the level, volume, and temperature of products in storage tanks, but they're usually connected to sirens, emergency shutoff valves, ventilation systems, and peripherals like fuel dispensers.
"Part of what makes these devices attractive to security researchers, or a malicious actor for that matter, is the potential ability to control physical processes that could lead to disastrous consequences if they are abused in unintended ways," Umbelino noted.
As Umbelino explained, "We found vanilla reflected cross-site scripting (XSS). The authentication bypasses were direct path access. The command injections lacked filtering. There were hardcoded administrator credentials. The arbitrary file read was a direct path traversal access, yielding admin credentials. The SQL injection could be exploited aided by full SQL error logs."
The vulnerabilities are as follows:
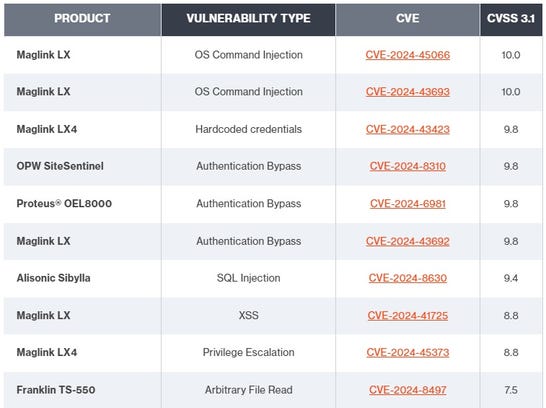
Source: Bitsight TRACE.
As an example of those consequences, attackers could exploit the bugs to change the amount of liquid a tank is capable of taking on, while also tampering with overflow alarms. The result could be an undetected tank overflow, which could cause gas spills and environmental chaos.
And as Umbelino explained in the post, "The most damaging attack is making the devices run in a way that might cause physical damage to their components or components connected to it. In our research, we've shown that an attacker can gain access to a device and drive the relays at very fast speeds, causing permanent damage to them."
Other bad outcomes include making the systems inaccessible via denial of service (DoS), exposing competitive operations data (delivery dates, pricing, inventory intel, types of alarms, etc.), or the loss of compliance data leading to potential regulatory fines. In a DoS scenario for instance, an attack could "lead to downtime and would usually require human intervention," Umbelino explained in the posting. "In fact, these types of attacks are currently ongoing, with claims of exploitation of at least one brand of devices for which we published a vulnerability on just two weeks ago."
Critical Infrastructure Under Increasing Cyber Threat
The critical infrastructure threat landscape continues to be a thorny problem for security practitioners, starting with the fact that ICS systems and the operational technology (OT) that controls them are designed to prioritize reliability and efficiency, not security.
"As a result, they often lack modern protections," Umbelino noted. "In addition ... vendors recently started to integrate them with newer technology to improve efficiency and remote access and this significantly changes their threat model. Of course, there is also a lack of cybersecurity experts that are familiar with ICS systems. It is hard to find vulnerabilities if no one is looking for them."
Threat actors have taken notice: Chinese APTs like Volt Typhoon and others are looking to gain a foothold within physical infrastructure, for operational espionage as well as cultivating the potential for disruptive attacks. Ransomware gangs have their own reasons for targeting ICS, as seen in the infamous Colonial Pipeline cyberattack.
"While not related to the vulnerabilities we found, there is a group consistently claiming ICT/OT disruption in the Ukraine-Russia war, including ATG systems," Umbelino says. "In this tweet, we can see an OPW ATG system being targeted, but they claim to have affected many other ICT/OT devices too, indicating that attackers do see these elements within critical infrastructure as a target."
CISA itself has flagged increased threats to water supply organizations, power plants, manufacturing, telecom carriers, military footprints, and more — attacks that are largely being spearheaded by APTs backed by China, Russia, and Iran.
So far, defenders have headed off catastrophic attacks at the pass, and there's no reason to expect mass gas spills anytime soon, given the complexity and sophistication required to exploit the bugs, but it's important to stay ahead of the risk.
"It’s not just about fixing vulnerabilities, it’s about adopting security practices that make them difficult to exist in the first place," Umbelino explained in the analysis. "And it is not just about the vulnerabilities themselves, it's about their exposure. Organizations need to understand they should not expose these types of critical systems to the public Internet. They need to effectively assess their exposure, understand their current risk and start addressing such issues, regardless of vendors ability to update their systems in a timely fashion."
Security researchers also have an important role to play, he adds, noting that stakeholders should be expanding their ICS focus.
"We should start paying more close attention to these types of systems that control very important parts of our society and that, if abused, can have a physical effect on the world, sometimes catastrophic," Umbelino says. "We need to systematically discover, classify and mitigate the risk of them being openly exposed to the Internet faster than the attackers, and be able to communicate that risk to all affected parties. It is not an easy task."
About the Author
You May Also Like
Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025Shift Left: Integrating Security into the Software Development Lifecycle
Mar 5, 2025




_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)