Industrial Systems See More Vulnerabilities, Greater ThreatIndustrial Systems See More Vulnerabilities, Greater Threat
The makers of operational technology and connected devices saw reported vulnerabilities grow by half in 2021, but other trends may be more disturbing.
March 7, 2022

The real threats to industrial control systems (ICS) became clearer in 2021, as the number of vulnerabilities discovered in operational technology (OT) devices and the systems that manage those devices jumped by more than half, while ransomware groups continued to target manufacturing and critical infrastructure.
The number of vulnerabilities reported in 2021 increased 52% to nearly 1,440, compared with the previous year, according to industrial cybersecurity firm Claroty's biannual report released last week. In addition, cybersecurity researchers branched out — 21 of the 82 vendors affected by security flaws in their software or firmware had not previously had vulnerabilities reported in their systems. Nearly two-thirds of the discovered security issues could be exploited remotely, Claroty's report stated.
The increase in vulnerabilities — as well as researchers' forays into previously explored vendors' products — shows that there is greater interest in industrial control systems, says Amir Preminger, vice president of research at Claroty.
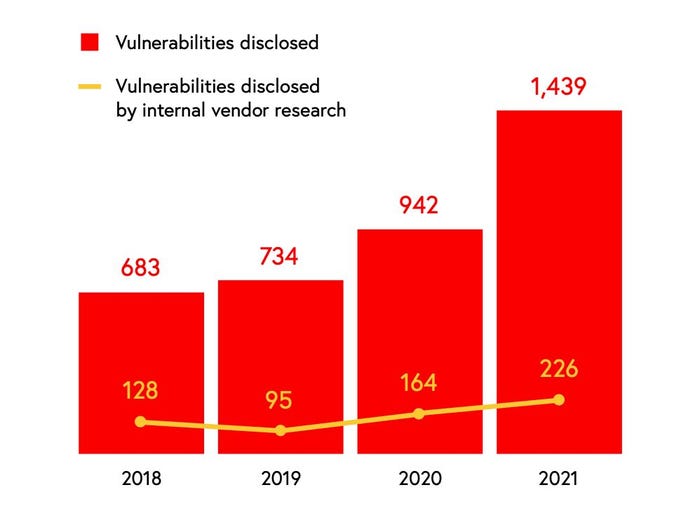
Reported ICS vulnerabilities increased by half in the past year, with an increasing number found internally. Source: Claroty Biannual ICS RIsk & Vulnerability Report, 2H 2021
"They [attackers] are trying to learn and gain access to industrial control systems, and these vulnerabilities are going to be their playground," he says. "A lot of the vulnerabilities that we have seen do not require high complexity to exploit, and when you talk about ICS, the barrier is very very low — you don't have to hack three layers of the cloud to exploit these."
The Colonial Pipeline Wake-up Call
II and OT have become significant concerns for cybersecurity policy-makers because, by their nature, they turn digital threats into physical risks. The ransomware attack on the IT systems of petroleum-delivery firm Colonial Pipeline in May 2021, for example, led to the business shutting down oil and gas deliveries, resulting in surging gas prices and shortages at the pump.
In addition, cybersecurity researchers have seen an increased focus on industrial control systems, because attackers have targeted operational technology in the run-up to the Ukraine War. On Feb. 26, for example, the US Cybersecurity and Infrastructure Security Agency (CISA) warned that Russia attackers had released significant attacks prior to the invasion of Ukraine, using two wiper programs to cause outages in government services.
Overall, attacks against critical infrastructure and industrial control systems have become more prevalent because an increasing body of research has given attackers a greater understanding of the systems and because cybercriminal schemes — most notably, ransomware — has made attacks against operational systems profitable, Dean Parsons, a certified SANS instructor and industrial cybersecurity professional, wrote in a SANS report released last week.
"We are seeing adversaries are being more clever to attack industrial environments, because they see a quicker to pay and pay more," he says. "These threats will not go away because the adversaries are seeing a return on their investment."
Because attackers also have more access to research on OT and ICS, that barrier to entry has practically disappeared. As a result, more vendors of industrial control systems, operational technologies, and Industrial Internet of Things (IIoT) devices are facing reported vulnerabilities in their products, according to the Claroty report. While Siemens, a major provider of industrial control technology, continues to be the vendor with the most reported vulnerabilities — 251 in the second half of 2021 — a quarter of the vendors in the second half and a third of the vendors in the first half did not have a vulnerability discovered in the past 12 months.
"These are good examples of vendors that have had no CVE [identified vulnerability] in their products," suddenly finding their technology under the microscope, Claroty's Preminger says." It is not due to the fact that they don't have vulnerabilities. The increase is from security researchers finally getting ahold of the technology and being able to conduct research."
Patching Conundrum
Only 69% of the ICS vulnerabilities discovered in the second half of 2021 could be fully remediated, highlighting another issue of industrial control systems and OT — the difficulty in updating software and devices that are part of critical infrastructure.
"These cycles can take significantly longer than traditional IT patch management, often making mitigations the only remediation option open to defenders," Claroty stated in its report. "Vendors and internal security analysts and managers must also prioritize tracking of vulnerabilities in end-of-life products and in products where updates may be challenging or downtime is unacceptable."
While vulnerabilities are increasing, they are not the best measure of the risk facing manufacturers, since many companies — such as Siemens — are proactively finding the issues and closing them before attackers can exploit them. More important is that companies understand the actions that attackers are taking, whether exploiting specific vulnerabilities or finding other ways of attack critical infrastructure, says the SANS Institute's Parsons.
ICS and OT security has different considerations than IT security, and they cannot be handled the same way, Parsons says.
"Sure there are vulnerabilities there, but we should not focus on the vulnerabilities, we should focus on what the adversaries are doing," he says. "We need to have more network-specific visibility — without that, we are literally blind to what attackers are doing to the industrial control systems. Visibility is key to getting ahead of this stuff."
In fact, 86% of companies that hired a cybersecurity provider had a lack of visibility across their operational technology networks, allowing external connections to their OT systems, according to a report by critical infrastructure security firm Dragos. The cybersecurity provider found that two groups — Conti and LockBit 2.0 — had made extensive use of industrial firms' lack of visibility, accounting for 51% of ransomware attacks against companies.
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025



_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)
_Brain_light_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)