A cloud with a finger pointing to the word API_Elena_Uve_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
Сloud Security_Elena_Uve_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
3 Use Cases for Third-Party API Security3 Use Cases for Third-Party API Security
Third-party API security requires a tailored approach for different scenarios. Learn how to adapt your security strategy to outbound data flows, inbound traffic, and SaaS-to-SaaS interconnections.

Ask the Experts
Read MoreFEATURED THREAT MONITOR
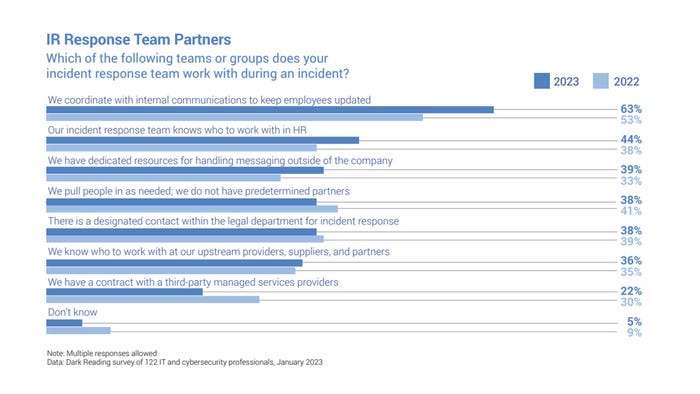
Effective Incident Response Relies on Internal and External Partnerships
Dark Reading research finds increased collaboration between security incident responders and groups within the HR, legal, and communications functions.


_Aleksey_Funtap_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)



_Elena_Uve_Alamy.jpg?width=300&auto=webp&quality=80&disable=upscale)


_Aleksey_Funtap_Alamy.jpg?width=300&auto=webp&quality=80&disable=upscale)






_Zoonar_GmbH_Alamy.jpg?width=300&auto=webp&quality=80&disable=upscale)








