Featured on The Edge Threat Monitor
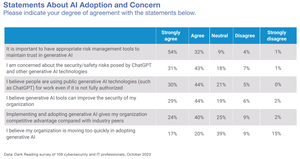
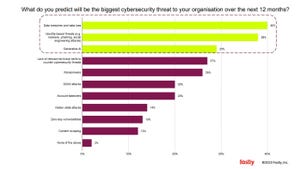
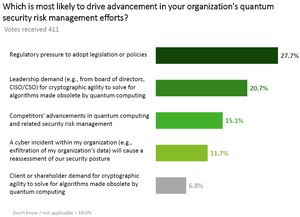
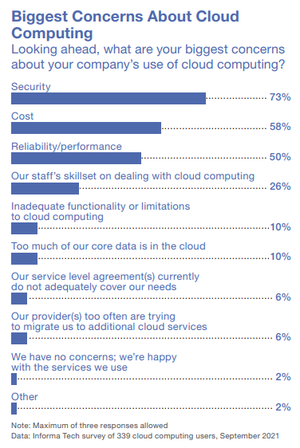
A chart from the 2024 Strategic Security survey.
Сloud Security
Managing Cloud Risks Gave Security Teams a Big Headache in 2024Managing Cloud Risks Gave Security Teams a Big Headache in 2024
The results of Dark Reading's 2024 Strategic Security Survey suggest that security teams continue to grapple with the challenges that come with increased cloud adoption, such as data visibility and loss of controls. Managing cloud risks will be a focus for security teams in 2025.
More from The Edge Threat Monitor
Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox.