Commentary
thumbnail
Perimeter
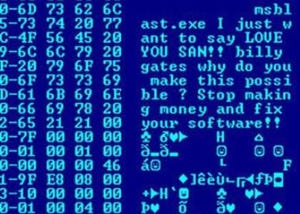
Making The Security Case For A Software-Defined PerimeterMaking The Security Case For A Software-Defined Perimeter
With SDP, organizations can create an 'invisible' infrastructure that only authorized users and devices can access. Here’s why it’s time has come.
byStephen Treglia, JD, HCISPP, Legal Counsel & HIPAA Compliance Officer- Investigations, Absolute Software
Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox.


































_santoelia_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)